Resource Center
For current and prospective customers

Resources
Whether you’re a current customer or prospective customer, we want to help you keep your people safe, and businesses running. Learn from our customers and from industry experts on best practices, solution information, and use cases for better critical event management within your organization.
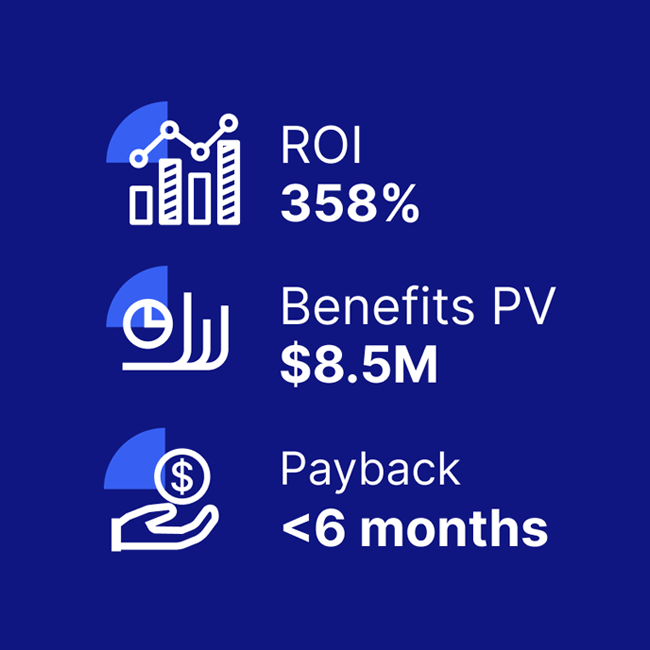
Significant ROI from critical event management solutions
A composite organization comprised of interviewees with experience using the CEM platform achieved a 358% ROI and US$8.5M in three-year risk-adjusted benefits, according to a commissioned Total Economic Impact(TM) Study by Forrester Consulting.
This includes:
- $3M in efficiency gains
- $2M saved in reduced IT downtime
- $1.5M in security team productivity gains
Discover the value Everbridge can bring to your organization from our ROI calculator, checklist, and full TEI study.

Everbridge University
Prepare your staff with free notification and best practices training.
Everbridge University provides your team with the skills, techniques, concepts, and best practices needed to correctly relay critical communications and manage incidents, allowing you to redeem the full value from your investment.